| No. | Type of Malicious | Descriptions |
|---|---|---|
| 1 | XSS |
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. When a malicious script is injected into the code of an otherwise trusted website, allowing potentially sensitive user data such as cookies to be accessed. |
| 2 | SQL Injection |
SQL injection is a code injection technique, used to attack data-driven applications, in which malicious SQL statements are inserted into an entry field for execution. A successful SQL injection exploit can extract sensitive information like read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the content of a given file present on the DBMS file system and in some cases issue commands to the operating system |
| 3 | Clickjacking |
Clickjacking is a malicious technique of tricking a user into clicking on something different from what the user perceives, thus potentially revealing confidential information. The attacker can take control of the user computer which can turn system features on and off, such as enabling your microphone and camera when a Javascript prompt asks for permission to access this information. It could also pull location data from your computer or other details that could facilitate future crimes. |
| 4 | High | Expose to the vulnerability, quite easy to penetrate and compromise, need a skill to perform the attack |
| 5 | DDoS |
A Distributed Denial-of-Service (DDoS) attack occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers. A DDoS attack uses more than one unique IP address or machines, often from thousands of hosts infected with malware Simply, the attack will exhaust network resources unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. |
| 6 | Credential Stuffing |
Credential stuffing is a type of cyberattack in which stolen account credentials, typically consisting of lists of usernames and/or email addresses and the corresponding passwords, are used to gain unauthorized access to user accounts through large-scale automated login requests directed against a web application |
| 7 | Social Engineering |
Social engineering is the psychological manipulation of people into performing actions or divulging confidential information. These human hacking scams lure unsuspecting users into exposing data, spreading malware infections, or giving access to restricted systems. |
What is Security Header?
Headers are part of the HTTP specification, defining the metadata of the message in both the HTTP request and response. While the HTTP message body is often meant to be read by the user, metadata is processed exclusively by the web browser and has been included in HTTP protocol since version 1.0.
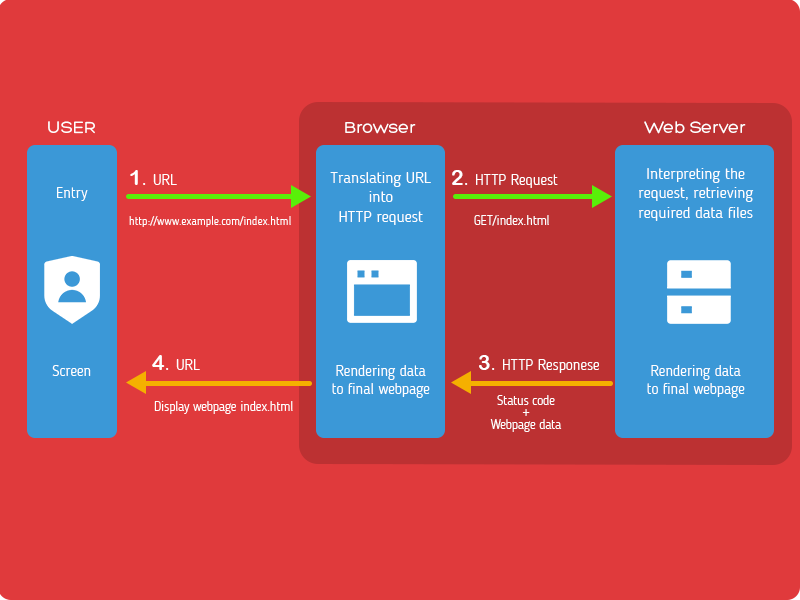
Why is Security Header Important?
User will only see a graphical interface on any website (no.1 and no.4 in the graphic), but between your browser and web server, the HTTP Request and HTTP Response (no. 2 and no.3 in the graphic) play an important role. While request, the good web server should include proper security header in HTTP response to ensure the connection is secure and intact.

What is SSL?
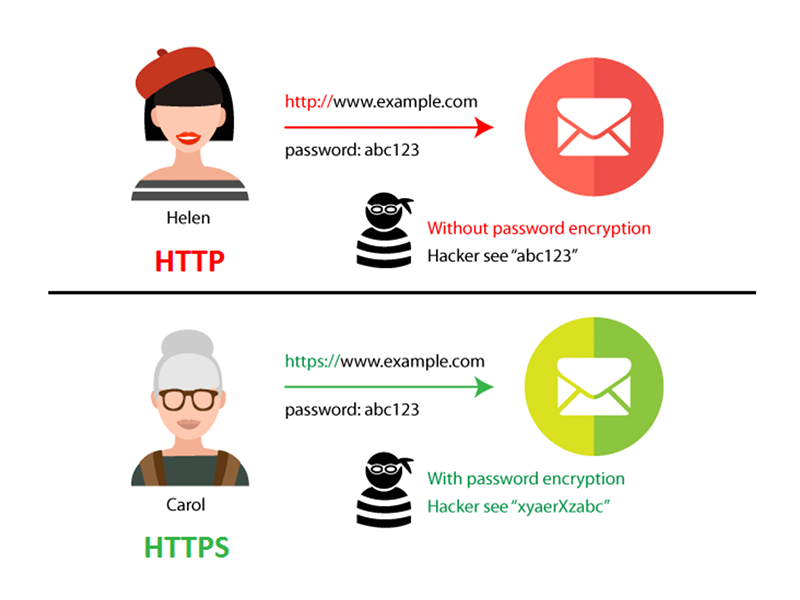
SSL is a HTTP with Secure Socket Layer implemented or HTTPS. The Primary reason why SSL is used is to keep sensitive information sent across the Internet encrypted so that only the intended recipient can access it. This is important because the information you send on the Internet is passed from computer to computer to get to the destination server.
Why is Security Header Important?
The primary reason why SSL is used is to keep sensitive information sent across the Internet encrypted so that only the intended recipient can access it. This is important because the information you send on the Internet is passed from computer to computer to get to the destination server.

