CVSS Scoring Summary
| Severity Level | Score Value | Description |
|---|---|---|
| Informational | 0 | Informational risk – no impact at all. |
| Low | 0.1 - 3.9 | Very low risk, mostly informational issues, vulnerability, need to have access directly to the target to perform the attack. |
| Medium | 4.0 - 6.9 | Expose to the vulnerability, quite easy to penetrate and compromise, need some other access before can perform the attack. |
| High | 7.0 - 8.9 | Expose to the vulnerability, quite easy to penetrate and compromise, need a skill to perform the attack |
| Critical | 9.0 - 10.0 | Very expose to the vulnerability, easy to penetrate and compromise your system without any deep technical skill to attack |
Lighthouse Scoring Summary
| Severity Level | Score Value | Description |
|---|---|---|
| Fast | 90 - 100 | Good Performance - you are doing great! |
| Moderate | 50 - 89 | Needs Improvement - There is some changes could be implemented for better results! |
| Slow | 0 - 49 | Poor Performance - Consult to our experts for further inspection! |
What is CVSS
The Common Vulnerability Scoring System is a free and open industry standard for assessing the severity of computer system security vulnerabilities. The calculation focusses on Security SEVERITY level only. Scores are calculated based on a formula that depends on several metrics that approximate ease and impact of an exploit. Scores range from 0 to 10, with 10 being the most severe
Why CVSS
CVSS attempts to assign severity scores to vulnerabilities, allowing responders to prioritize responses and resources according to threat. The calculation of CVSS is to now the Severity level, not Risk!

How CVSS Calculated
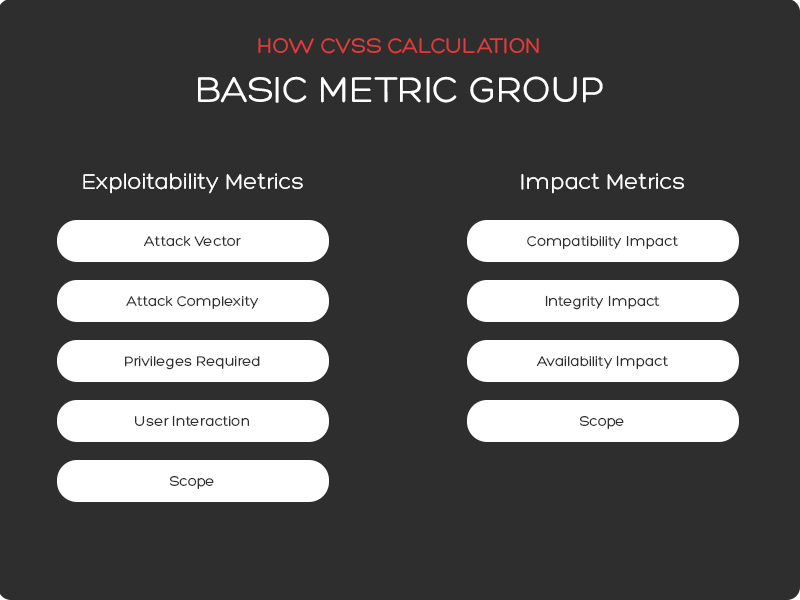
The calculation is based on several based matrices, namely:
- Exploitability – Exploitability metrics are made up of
characteristics of the vulnerable component, with Exploitability being made up of four
further sub-components.
- Attack Vector – this score varies based on the level of access required to exploit a vulnerability. The score will be higher for exploits that can be executed remotely (i.e. outside of a company’s network) than for exploits that require physical presence (i.e. must have access to a physical port on an appliance or access to a local network inside of a private data center).
- Attack Complexity – this score varies based on the factors outside of the attacker’s control that are required to exploit the vulnerability. The score will be higher for exploits that require additional work on the attacker’s part, such as theft of a shared secret key or a man-in-the-middle attack, than for an attack that requires no such additional effort.
- Privileges Required – this score varies based on the privileges required for the attacker to conduct the exploit. A vulnerability that requires administrative privileges to exploit will have a higher score than an exploit that requires no authentication or escalated privileges on the attacker’s part.
- User Interaction – this score varies based on whether the attacker must recruit either a willing or unwitting participant in order to complete their task. The score will be higher if the attacker can operate autonomously, with no participation from a user.
- Scope – Scope relates to whether a vulnerability in one component can propagate to other components. The scope score is higher if propagation is possible. Examples of scope include ability to access and exploit the underlying operating system after exploiting a vulnerability in a software application, or an attacker accessing a backend database after successfully exploiting a vulnerability in a web server.
- Impact – Impact focuses on the actual outcome that
an attacked can achieve as a result of exploiting the vulnerability in question. Impact
metrics are comprised of three sub-metrics – Confidentiality, Integrity, and Availability.
- Confidentiality – this score varies on the amount of data that the attacker gains access to. It will be higher if all data on the impacted system is accessible by the attacker, lower if no data is accessible.
- Integrity – this score varies based on the ability of the attacker to alter or change data on the impacted system. If complete, or severely consequential modifications to data are possible, this score will be high.
- Availabilityy – this score varies based on the loss of availability of the exploited system. The score will.
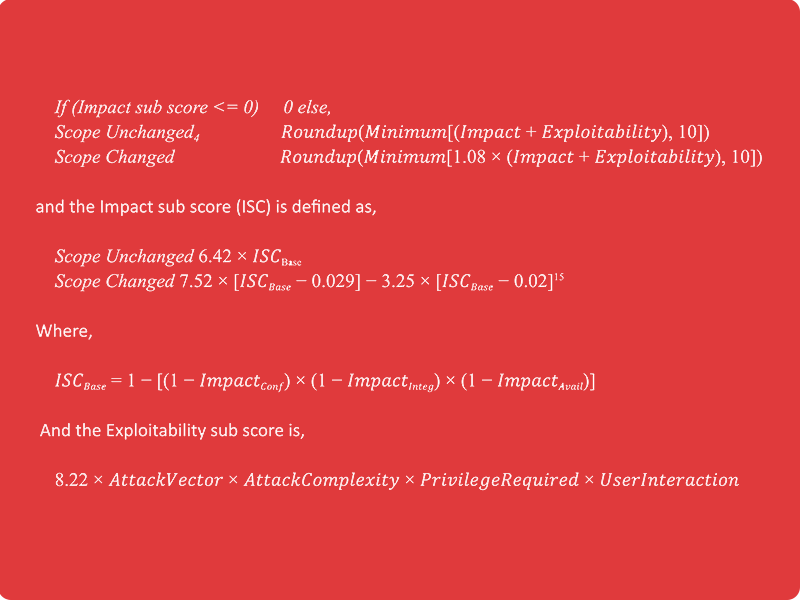
The Base Score
The Base Score is a function of the Impact and Exploitability sub score equations. Where the Base score is defined as,
How Lighthouse Calculated

Every webpage that is crawled by a search engine is evaluated with a score from 5 categories: Performance, Accessibility, Best Practices, SEO and PWA. This is given a score between 0 - 100. The better your lighthouse score is will affect how high up your webpage will appear on a search engine.
Each of these categories are judged on the following:
- Performance is judged on how quick it takes your webpage to load.
- Accessibility is judged by how accessible your website is. Especially forusers who might require technology such as screen reader or have diificulty with colors.
- Best Practices are judged by factors which will usually only be apparent to developers. This will be on code health, for example. Using deprecated Libraries/APIs. Asking for permission if you want the users locations and making sure that it is a secure connection of HTTPs.
- SEO (Search Engine Optimisation) is judged by making sure the page is optimised for search engine results. This is a large area of website design but some simple examples could be Header names and using keywords. Making sure images have descriptive names so a search engine can label them.
- PWA (Progressive Web Apps) does not receive a score. It is either there or not. This is still a rather early technology, but makes websites run faster on repeated views.
